A technically minor attack like a defaced web page may or may not be as devastating as a backend server breach. What about a multi-vector DDoS (distributed denial of service) attack? The security management process helps your organization get a better understanding of your attack surface i.e., exposure to risk. It is important for your organization to perform your own risk analysis to determine how costly a data breach or offline system is.
An incident response plan detailing what to do in the event of a cyber breach is key to helping your organization recover. Technology changes, vendors change, and people change around your cyber landscape so it is important to keep your incident response plan up to date and relevant. For many organizations this is a perpetual process.
The first part of your organization’s solution is to gather your management team and ensure that IT security is an included and thorough part of your risk management plan. Healthcare, education, government, and financial organizations are required to include information security and many industry catered templates or programs can be leveraged.
Security risk management is an important business and financial undertaking. It includes identifying important assets to an organization and helps to determine the value or emphasis that should be placed on protecting those assets. These assets can be information (data), facilities, people, products, or systems. A complete risk management program is not only required for many organizations but imperative to their survival and financial well being.
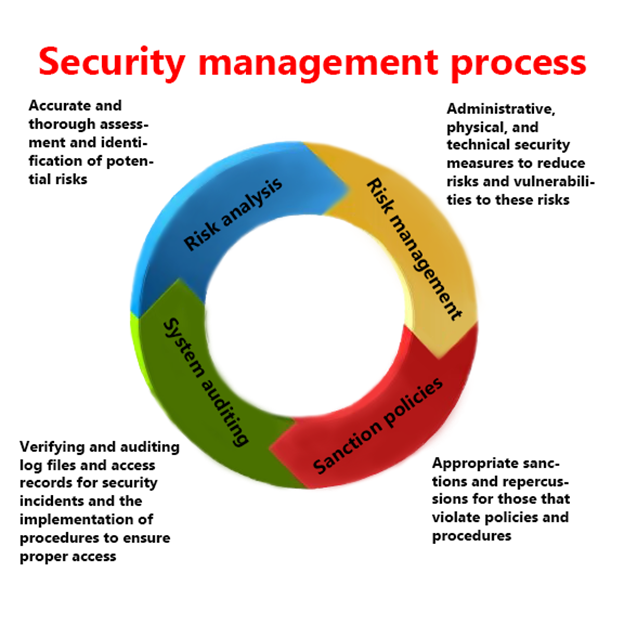
The only way to measure the performance of a risk management program is to perform audits. Audits help to inform you of whether or not your administrative, physical, or technical safeguards are working and properly in place. If a security incident uncovers a new gap in your security management plan then your team must account for this new gap or vulnerability.
Your cyber security plan should consider compromised users and ways to mitigate and trap such users. It’s all in the log files. Log file correlation and automation is a good practice to adopt, and getting problems to the human awareness and response level is ultimately what your organization needs to successfully mitigate a cyber event.
Successful attacks take time to implement and realize. Most all major cyber incidents like that of retail chain Target or the Playstation network of Sony go unnoticed for weeks or even months. Recent attacks in the news show that organizations are often times lazy about log file auditing or simply don’t know what they are looking at.
